For comprehensive cleanup, you’ll really need to use multiple instruments and procedures based upon how and in which the malicious code and links are inserted.Link exchanges: When Internet websites conform to link to each other as a way to improve rankings, that reciprocal linking is frequently seen as manipulative (although not always).Your link
 Rick Moranis Then & Now!
Rick Moranis Then & Now! Brian Bonsall Then & Now!
Brian Bonsall Then & Now! Joseph Mazzello Then & Now!
Joseph Mazzello Then & Now! Melissa Joan Hart Then & Now!
Melissa Joan Hart Then & Now!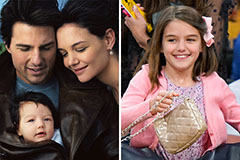 Suri Cruise Then & Now!
Suri Cruise Then & Now!